Openplatform.xyz Follow @openplatformxyz
Placeholder for our stuff related to Telecom, IT, Internet of things (IOT), ESP8266, Raspberry Pi
SIPp with SIP-I (ISUP) support
SIPp with SIP-I support works on Linux.
Download sipp source code (tar.gz) from
https://github.com/SIPp/sipp/releases
You can use wget to
download
# wget https://github.com/SIPp/sipp/archive/v3.6.0.tar.gz
Unpack the files
# tar -zxvf v3.6.0.tar.gz
Change directory to sipp folder
# cd sipp-3.6.0
You have four options to compile SIPp:
a) Without TLS (Transport
Layer Security), SCTP or PCAP support
./configure
b) With TLS
support
./configure --with-openssl
c) With PCAP play support:
./configure --with-pcap
d) With SCTP support:
./configure
--with-sctp
e) You can also combine these various options, e.g.:
./configure --with-sctp --with-pcap --with-openssl
After that give make command
# make
See more details on https://sipp.readthedocs.io/en/v3.6.0/installation.html#installing-sipp
Errors and Solutions normally encountered
Error: /bin/sh: gcc: command not found
Solution: # sudo yum
install gcc
Error: /bin/sh: g++: command not found
Solution: # sudo yum
groupinstall 'Development Tools'
Error: sipp.hpp:52:20: fatal error: curses.h: No such file or
directory
Solution: # sudo yum install ncurses-devel ncurses
Error: auth.c:32:10: fatal error: openssl/md5.h: No such file or
directory
Solution: # sudo yum install openssl
# sudo yum install openssl-devel
Error: send_packets.c:44:10: fatal error: pcap.h: No such file or
directory
Solution: # sudo yum install libpcap
# sudo yum install libpcap-devel
configure: error: SCTP library missing
Solution: # sudo yum install
lksctp*
finaly you will witness make completion.
make[1]: Leaving directory
`/root/sipp-3.6.0'
SIPp is ready. Lets Test it.
# ./sipp -v
SIPp v3.6.0-TLS-SCTP-PCAP-RTPSTREAM.
Sample UAS Script
Sample UAC Script
How to extract ISUP data from wireshark pcap file and use in a scenario script?
Open SIP-I pcap file in wireshark.
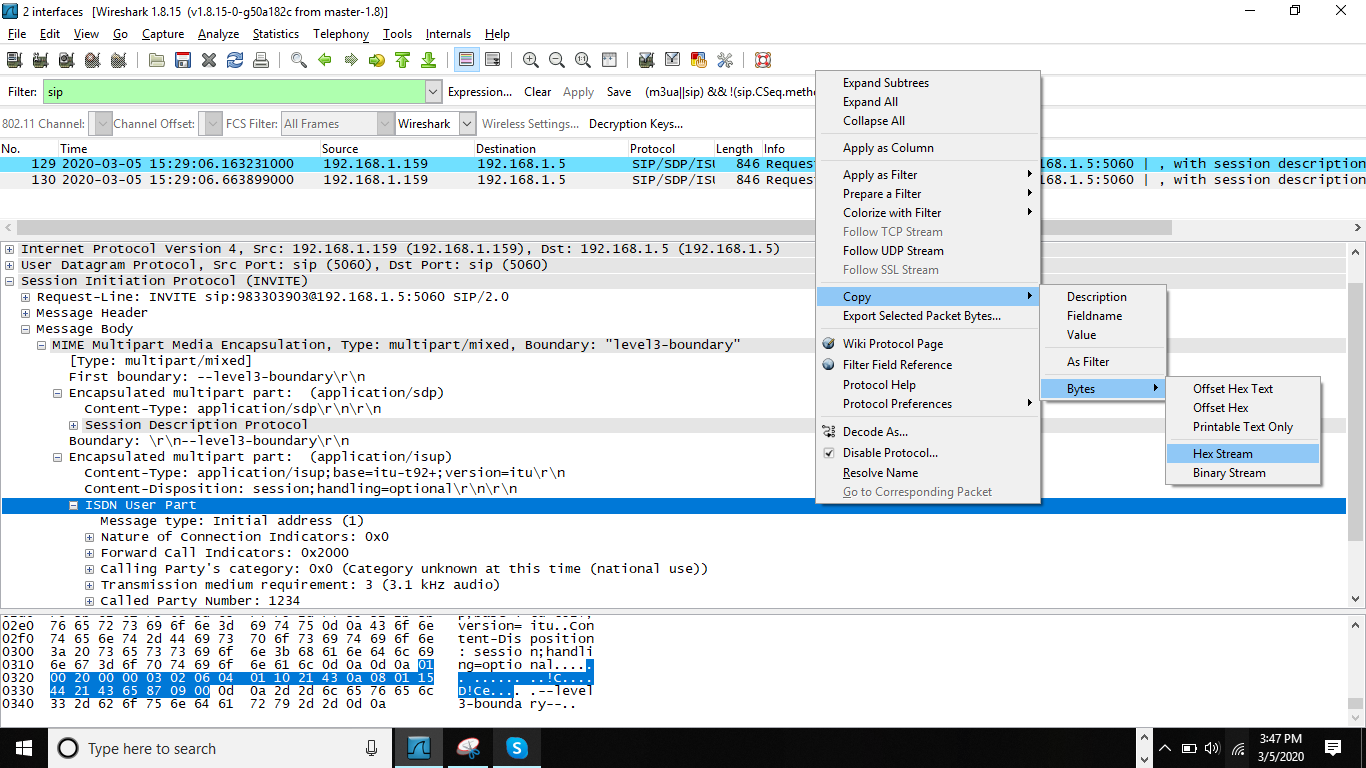
Select sip message in wireshark packet list pane.
Expand message
in packet detail pane and look for "ISDN User Part"
Right click on
"ISDN User Part", click on Copy --> Bytes --> Hex Stream
You will get something like this
010020000003020604011021430a08011544214365870900
Insert \x at start and after every two digits. Finaly it should look like below:
Use this string in --level3-boundary-- of sip message in scenario
Links:
https://raw.githubusercontent.com/shariramani/sipp-scenarios/master/sh_sipi_uac.xml
https://raw.githubusercontent.com/shariramani/sipp-scenarios/master/sh_sipi_uas.xml

Suresh Hariramani
I am an IOT enthusiast with more than 20 years of experience in the IT sector. Specializing in telecom service's; follow me for some very innovative and best in class IOT products as I unfold my knowledge and passion for the subject.

Vatsal Hariramani
Just me, myself and I, exploring the universe of uknownment. I have a heart of love and interests in technology, IOT and travel . And I want to share my world with you .
 Home
Home Internet Of Things
Internet Of Things Telecom
Telecom IT stuff
IT stuff About Us
About Us Contact Us
Contact Us Site Map
Site Map